Wiegand protocol is named after John R. Wiegand. He discovered the Wiegand effect. Which is a physical phenomenon in which a special wire produces small magnetic fields. So this magnetic effect is used to transmit information.
Indeed, over 90% of access control systems use the Wiegand protocol. This is the most common communication method to send information from the card reader to the controller.
The wiegand technology can also refer to the coding format of the card
Wiegand protocol
The Wiegand interface consists of a wire of three conductors called Data 0 (Green). Data 1 (White). And Ground (Black). It is a Wiegand wire.
Actually, John Wiegand revolutionized the access control industry in late 1970s with several new inventions based on “Wiegand Wire.”
He also created the Wiegand card by embedding 26 small pieces of wire within the base of the credential. Then Hi designed Wiegand reader to interpret the arrangement of the wires as someone swipes the card or approaches it to the reader.
In addition to this, he developed the Wiegand protocol as a way for the reader to send card data to the system where authorized credential values were stored.
The wire transmits either +5 VDC or 0 VDC signal as 1’s and 0’s, respectively, creating a binary data line for authenticating the scanned card’s credentials.
The 26-bit Wiegand format is the original and it is the most used. The diagram below shows its format
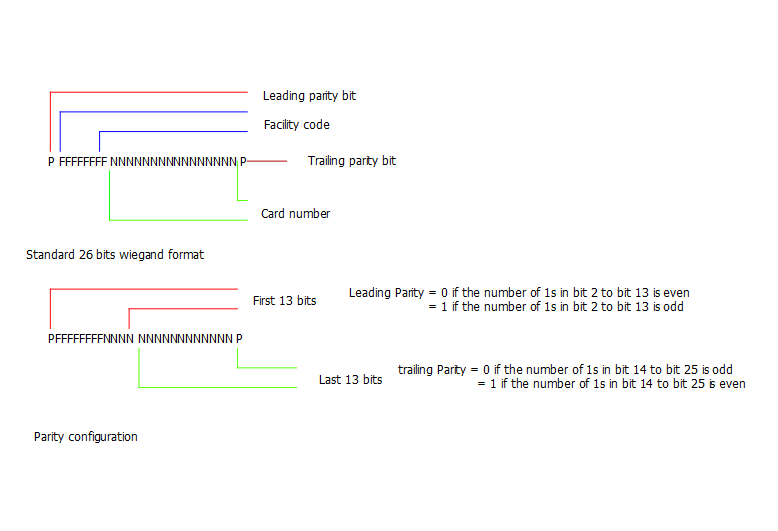
Limitation of Wiegand protocol
- There is no encryption of data transfer on wiegand protocol. This makes hacking easier
- The communication in wiegand protocol is unidirectional. As a result, the system is not able to re-quest status from the reader. It is also impossible to update the devices collectively, for example we need to update the readers manually. Therfore, it will not be an easy thing when it comes to a site with several readers
Conclusion
Wiegand technology revolutionised the security system industry since the 80’s. Most of security are working with this technology. Still it suffers from big vulnerabilities. As a result, it is obvious that for reader technology and capabilities to progress.
Access control actors recognized this need and came up with many solutions and a possible alternative such as an OSDP protocol (Open Supervised Device Protocol)
Valuable info. Lucky me I found your site by accident, and I’m shocked why this accident did not happened earlier! I bookmarked it.
Thank you for your kind comment Hairstyles