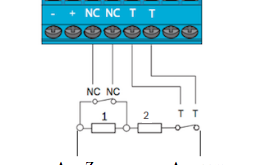
The security system is designed to secure a propriety or assets. But what if it is not secured itself ? Then to ensure security the system needs to be secure itself.
If the security system is broken or defeated, that means that it can’t successfully accomplish what it is designed for.
Fortunately, the systems are built in with capacity to supervise themselves. Manufacturers also provide tempered devices that can notice any disfunction. In addition, installers connect the devices in a way that the panels distinguish the three different situations which are:
- Normal situation
- Trouble
- Alarm
Not only the system parts need protection and supervision. But since systems are integrated on platforms such as Physical security information management. They are using internet protocol and IP technology. The software protection is another layer of security that we must add to protect the system.
This article will walk you through how to be sure that you are protected from any threat and that your system is protected on both sides software and hardware.
How to secure a security system software?

The trend in the security industry is toward IP solutions and internet protocol. As a result, it is imperative to secure the network infrastructure that hosts the integration platform. In this wake : it is recommended to :
- Use virtual local networks (VLAN), firewalls and
- Disabling not used network ports to avoid addition of devices
- Detection of link up and link down activity and lock down the connection of new devices
- Implementing a passwords management policy and changing all default passwords
- Providing basic training of the personnel, because security breaches occur as a result of human error or carelessness.
- Implementing a backup strategy and anticipate plans for possible need to recovery
- To control over installation programs in workstations
In addition, The organisation must apply access control and video surveillance on server rooms and network hardware installations. And we should pay more attention on all work stations.
How to secure a security system hardware?
securing equipment is another aspect of ensuring the system security.
First of all concealing the cable is a major step toward this goal. Secondly using the tempers on the equipment is another must in addition to the use of the end line resistors in the wiring.
Let’s see each of these techniques in detail in what follows.
Concealing the cable
The best way to conceal the cable is to fish through the wall and drill where we want to install the equipment. This is possible when the system installation is during the construction of the site.
If the wall concrete not possible to pass the cable through it. We use conduit, but it is not very aesthetic.
Cable concealers are also available in different colors to fit the colors of the wall.
Using tempers on the devices
Almost, all security system devices are built in with tempers.
The tempers are terminations on the device where we connect wire to prevent when the device’s cup is open. This prevents any sabotage on the equipment. It is important also to use tempers on the enclosures of the principal panels and the power supplies. They will alert in case those enclosures are open
Using end of line resistors
End of line resistors are little components that used to complete a circuit. The panel reads the value of the circuit and determines if it is normal or not.
The diagram bellow shows a normal zone with an end of line resistor. In this case, the panel reads 0 Ohm because the circuit is closed.
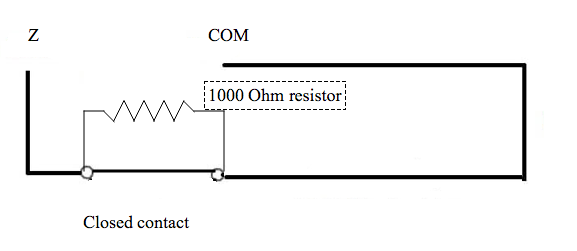
The following diagram shows an open circuit, it means that a system is under alarm. it reads 1000 Ohm of resistance.
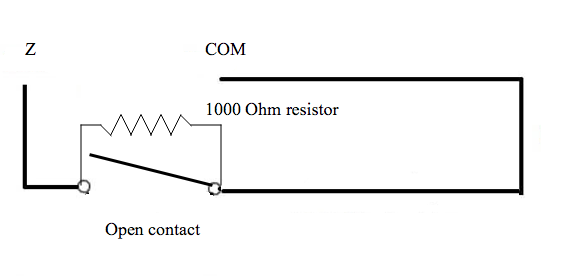
And follows a diagram of sabotaged circuit of security system with end of line resistor.
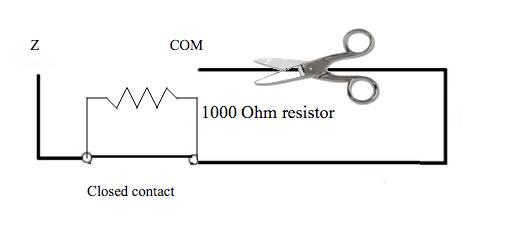
In case of sabotaged circuit. the panel will read an open loop which means that it will displays a trouble and asks for repair it.
In summary this is the 3 situation that the system will have and react to
- Closed loop : Normal situation
- Reads the resistor : Alarm situation
- Open loop : trouble
Conclusion
It is not enough to install a security system. It is important to protect it, otherwise it will fail. Moreover, as the systems are more and more integrated and are based on internet protocols. That is where the cooperation of security systems installers and IT departments comes into play to integrate the security systems in the global Cyber security of the organisation.