Access control cards have been around for decades. We are used to swiping our cards on a reader, but we are moving toward using our phones, our watches or bracelets to get in.
Access cards technology is constantly evolving, for it is linked to IT technologies. In this article, I am going to walk you through the evolution of access control credentials.
Mag stripe cards
Magstripe was the first technology used to carry data on a card. Like banking systems and credit cards, access control relied on it to embed user’s credentials since the 80s.
Proximity cards
Proximity cards mean that the contact between the card and the reader is not necessary.
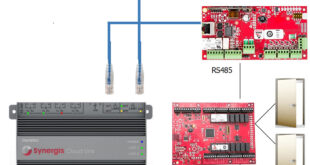
The card is built with an integrated circuit attached to an antenna. It becomes active with radio frequency identification protocol (RFID) when it is at a close range with a contactless low frequency (125KHz) reader.
Then the activation causes the card to provide its ID to the reader, then the process of identification and granting access goes on.
Limitations
The proxy card is easy to copy and to forge.
The card caries a simple ID number and can’t be encoded with multiple IDs or any other additional data attributes.
Smart access cards (High frequency cards)
Smart cards called also High frequency cards, came to address the proxy card’s limitations. Thus, the user ID is protected by authentication process between the card and the reader, this prevents the card to be copied. The high frequency cards are built with a chip where the user credentials are stocked. The card support read/write function. They are able to carry additional attributes data as well.
Limitations
The implementation of identity systems still relies on the ID of the chip, which is a proxy for the user’s identity. Since the chip is based on Application Specific Integrated Circuit (ASIC), this is a hard-wired integrated circuit.
Encrypted access cards
Smart cards allowed to carry more information on a chip card. They also helped address the limitation of reading and writing on the card as well. But still the problem of copying the card hovers. Because the chip stores the credentials, then, at a close range with the reader, it activates, then broadcasts the information within the chip.
That’s why the industry embraced the encryption solution. As a matter of fact, the credentials are encrypted. The reader must have the encryption key in order to read the card information.
The security industry tended to virtualize the credentials as well, and transform the card to a simple carrier of information. As a result, smartphones can also carry the credentials. So people can only use their phones to get access to their homes or jobs.
Some popular cards
Mifare desfire, IClass, and Seos cards are very popular access cards provided respectively by the NXP Semiconductor and HID. Let’s have a brief listing of the cards they are providing and which technology they are using to protect the user information.
Mifare and desfire cards
Mifare and desfire is a technology invented by NXP.
It introduced many generations of Mifare Desfire cards:
- Mifare desfire in 2002. It relies on open standards 3DES crypto algorithm.
- Mifare desfire EV1 in 2008. NXP moves to open standard AES crypto.
- Mifare desfire EV2 in 2016
- Mifare desfire EV3 in 2020
IClass SE cards and IClass Seos HID cards
IClass SE cards
They add encryption of the user identity and the data within the card’s chip. They call it Secure Identity Object ( SIO ).
IClass SEOS
IClass Seos implements an independence of the credential information from the underlying physical form factor.
This paves the way for the next generation of access credentials which is the use of smartphones.
Smartphones carrying access credentials
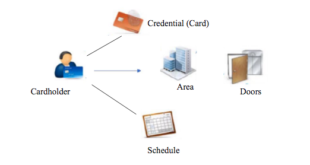
As I already mentioned, the security industry is tending to separate the credentials from the card or the physical access device. In other words, it draws a distinction between the physical credential which is a card, a device with an RFID chip that is presented to the reader and the digital credential that provides the proof of the ID.
The physical credential is only to carry the digital ID and protect it from being copied or modified.
It comes in different shapes, phone, key fobs, cards … etc. likewise the communication could be in different ways : RFID, Bluetooth, Wi-Fi …etc.
The smartphones allowing access or payment are the proof that this tendency is already there.
Access cards applications
Thanks to the ability of the chips to carry information and to the NFC communication protocol. Access cards are more and more popular. In addition to access control, you can see them in mobility like transport and mobile ticketing, parking, car and bike sharing. In micropayments and in loyalty and membership cards as well.
For more information about the subject, read our post :